In this post I will share the steps to create the Microsoft Certificate Authority Template to support for custom SSL certificate creation in VMware vSphere 6.7 .

Before jumping to the steps i will just give a intro to Certificate templates .Certificate templates are used to define the enrollment policy on the CA. First, an Enterprise CA can only issue certificates based upon the templates it is configure to use. Second, permissions set on the certificate template’s Active Directory object determine whether or not a user or computer is permitted to request a certificate based on that template. If a user does not have Enroll permissions on a particular template, the CA will deny any request submitted by the user for a certificate based on that template.
Certificate templates contain properties that would be common to all certificates issued by the CA based on that template. Windows includes several predefined templates, but Administrators also have the ability to create their own templates specific for their enterprise. When requesting a certificate, a client can just specify the template name in the request and the CA will build the certificate based upon the requestor’s information in Active Directory and the properties defined in the template.
Currently, there are three versions of templates:
Version 1 templates were introduced in Windows 2000, and can be used by Windows 2000, Windows Server 2003 (R2), and Windows Server 2008 (R2) Enterprise CAs. Version 1 templates Active Directory objects are created the first time an Enterprise CA is created in the forest. These templates were designed to reflect the most common scenarios for digital certificates in the Enterprise. Unfortunately, if you don’t like the settings we selected you’re pretty much out of luck. Creating new v1 templates, or editing the existing templates, is not supported. The only customization supported is to the permissions on the template.
Version 2 templates were introduced in Windows Server 2003 and are a vast improvement over v1 templates. First and foremost, v2 templates can be modified by an Enterprise Admin. In addition, the Admin can duplicate an existing v1 or v2 template to create a new v2 template, and then customize the result. Finally, v2 templates expose a larger number of properties that can be configured, and also expose some controls to take advantage of some other new features introduced in Windows Server 2003. One of these features, for example, is key archival. Version 2 templates can be used by Windows Server 2003 and Windows Server 2008 Enterprise or Datacenter Editions. On Windows Server 2008 R2, v2 templates can be used by a CA installed on Standard, Enterprise, Datacenter, Foundation and Server Core Editions.
Version 3 templates were introduced in Windows Server 2008. Version 3 templates have all the features of a version 2 template with two major additions. First, v3 templates support the use of Crypto Next Generation (CNG) providers, which means that the certificates support Suite B algorithms based on Elliptical Curve Cryptography (ECC). Second, v3 templates have a setting that instructs Windows to grant the Network Service account access to the private key created on the requesting computer. This is great for those certificates that will be used by applications or services that run as Network Service rather than Local System. Version 3 templates are supported by CAs installed on Windows Server 2008 Enterprise and Datacenter Editions. They are also supported by CAs installed on Windows Server 2008 R2 Standard, Enterprise, Datacenter, Foundation and Server Core Editions.
To create a template for vSphere environment we will use the default Web Server template on the CA server . We will perform a clone of the webserver template with some modification and a version 2 template will be created .
Creating a template for vSphere 6.x to use for Machine SSL and Solution User certificates
Log into your Windows Certificate Authority Server
Navigate to click Start > Run and type certtmpl.msc and click OK.
From the Certificates Templates Console you will see a list of different certificate templates , we will be creating a new template for use by the Machine SSL and Solution Users certificates by cloning Web Server Template.
Navigate to Web Server Template -> Right-click -> Select Duplicate Template.

Select Windows Server 2003 for backward compatibility.

Notes: If you have an encryption level higher than SHA1, you may select Windows Server 2008 / 2008 R2
Click the General tab and enter vSphere 6.7 as the name of the template in the Template display name field

Click the Extensions tab. Select Application Policies and click Edit and remove Server Authentication and click OK.

Select Key Usage and click Edit. Select the Signature is proof of origin (nonrepudiation) option. Leave all other options as default.

Click the Subject Name tab. Ensure that the Supply in the request option is selected and Click OK to save the template.

Adding a new template to certificate templates
Now that we have created the certificate template for vSphere 6.7 to use for Machine SSL and Solution User certificates . Next you have to add them to the list of template that we can select when submitting certificate request
Click Start > Run, type certsrv.msc, and click OK.
Right-click Certificate Templates and click New > Certificate Template to Issue.

Locate vSphere 6.7 from the list and Click OK.
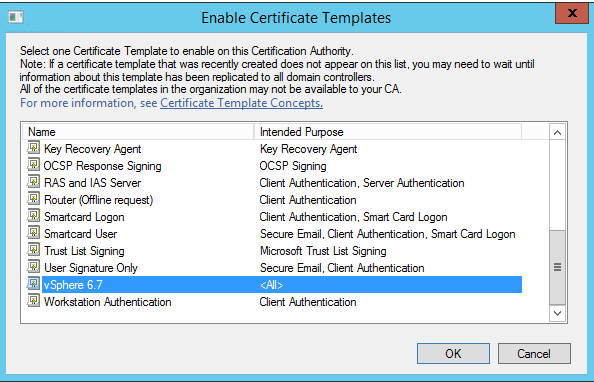
Now we have created a new vSphere 6.7 Certificate Template and it can be used while creating and replacing the Machine SSL certificate for VCSA .

