Every organization will have a firewall in their physical layer which helps to control the attack and secure the data center environment. Even though we have firewalls, attacks are happening, and services are going down. VMware NSX solution provides complete micro-segmentation in your Software-defined datacenter to secure the infrastructure from attacks.
By using micro-segmentation every machine can be isolated and in an easy way. With a few clicks, you can create security policies and manage everything from a central place. By using micro-segmentation distributed firewalling will be applied for every individual VM at the kernel level, and there is no option to bypass the networks and access the virtual machine.
To configure the micro-segmentation, first, you need to create a security group and place the VMs
Creating a Security Group
A security group is a collection of assets or grouping objects from your vSphere inventory.
Security Groups are containers that can contain multiple object types including logical switch, vNIC, IPset, and Virtual Machine (VM). Security groups can have dynamic membership criteria based on security tags, VM name or logical switch name. For example, all VM’s that have the security tag “web” will be automatically added to a specific security group destined for Web servers. After creating a security group, a security policy is applied to that group.
Here we are going to create two security group for Web Server and Web App and testing the micro-segmentation by configuring the rules.
Navigate to Home –> Network and Security
From Select Service Composer Select security groups
From Security Group Click on ‘+‘ symbol to add a group to Create Second Security Group for the Web Server VM
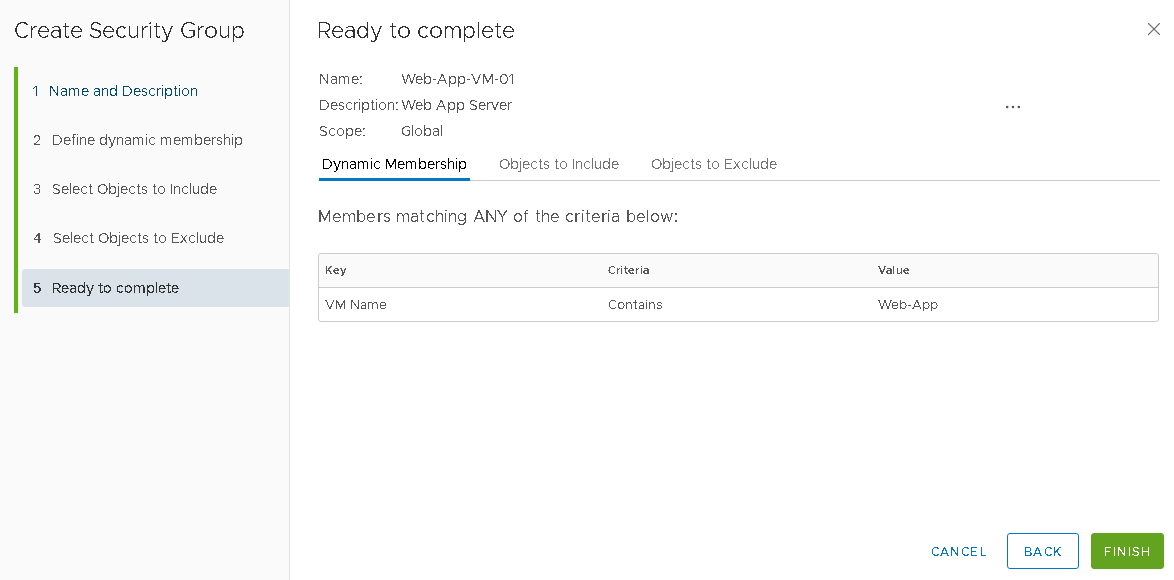
Provide a Name and Description and Clik Next
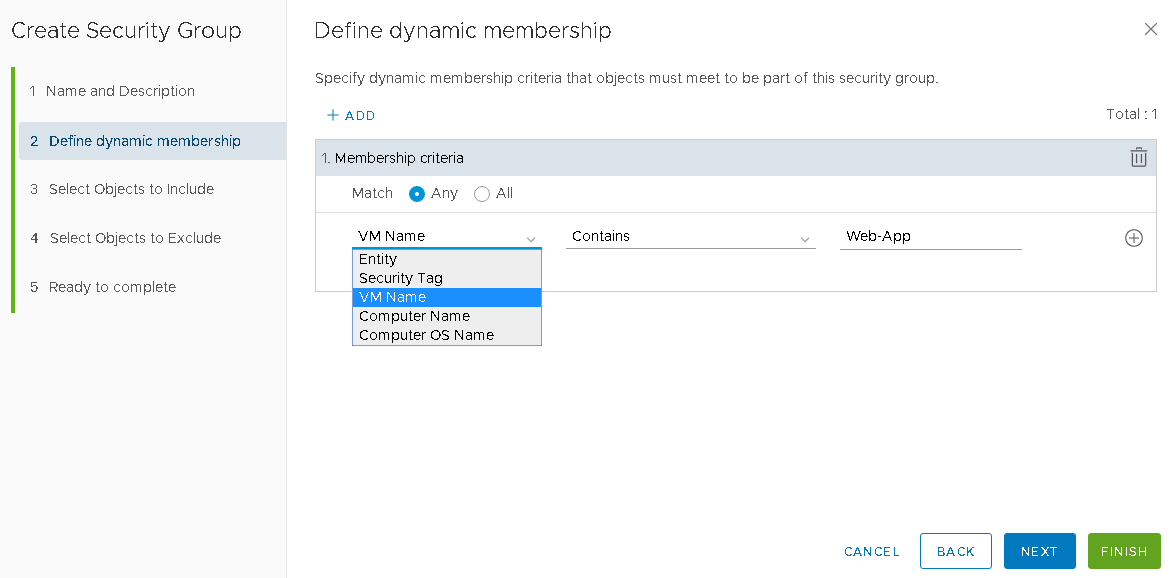
On the Dynamic Membership page, define the criteria that an object must meet for it to be added to the security group you are creating, and here we use VM Name, Contains Web-App, Clik Next
Note:-If you define a security group by virtual machines that have a certain security tag applied to them, you can create a dynamic or conditional workflow. The moment the tag is applied to a virtual machine, the virtual machine is automatically added to that security group.
Click Next
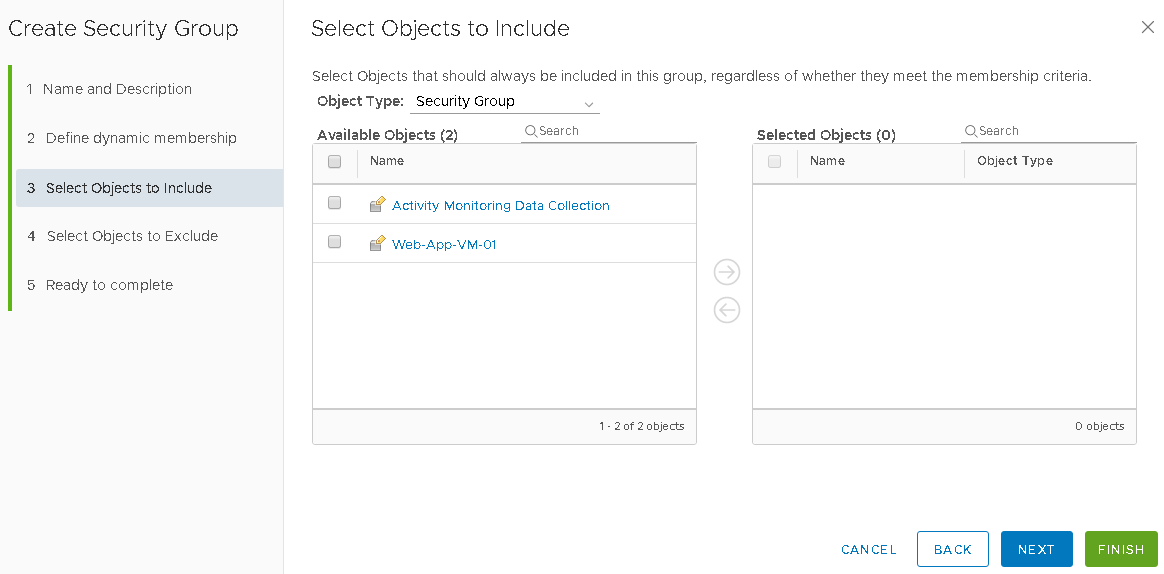
Note:- here you have the option to choose object types and select the objects since we define membership no actions required.
Click next
Click Finish to create the Security Group
Next, Let’s create another Security group
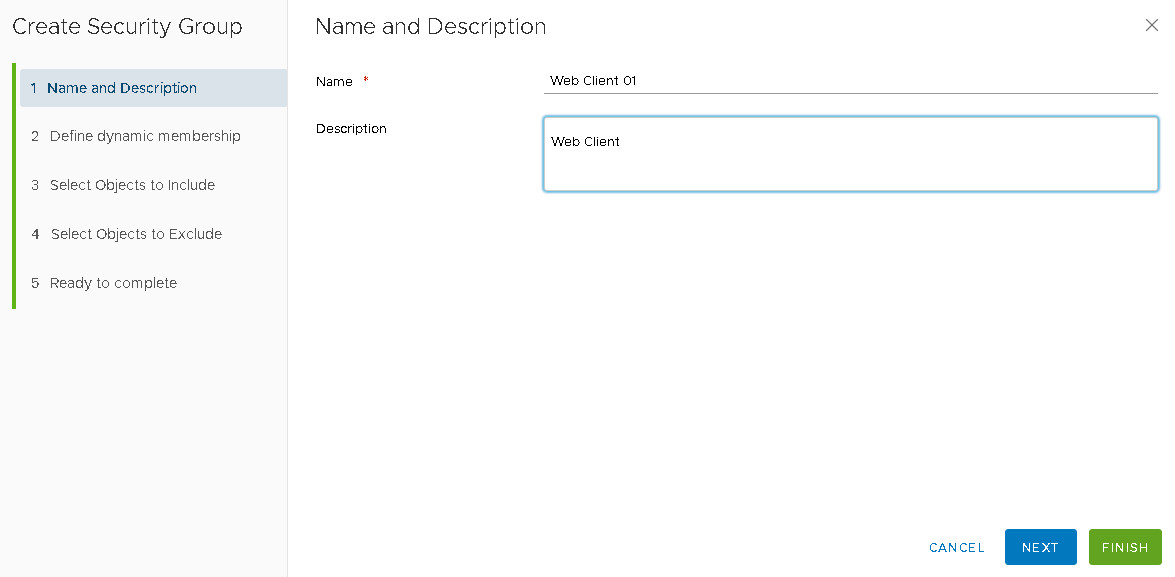
From Security Group Click on ‘+‘ symbol to add a group to Create Second Security Group for the Client VM
Provide a Name and Description
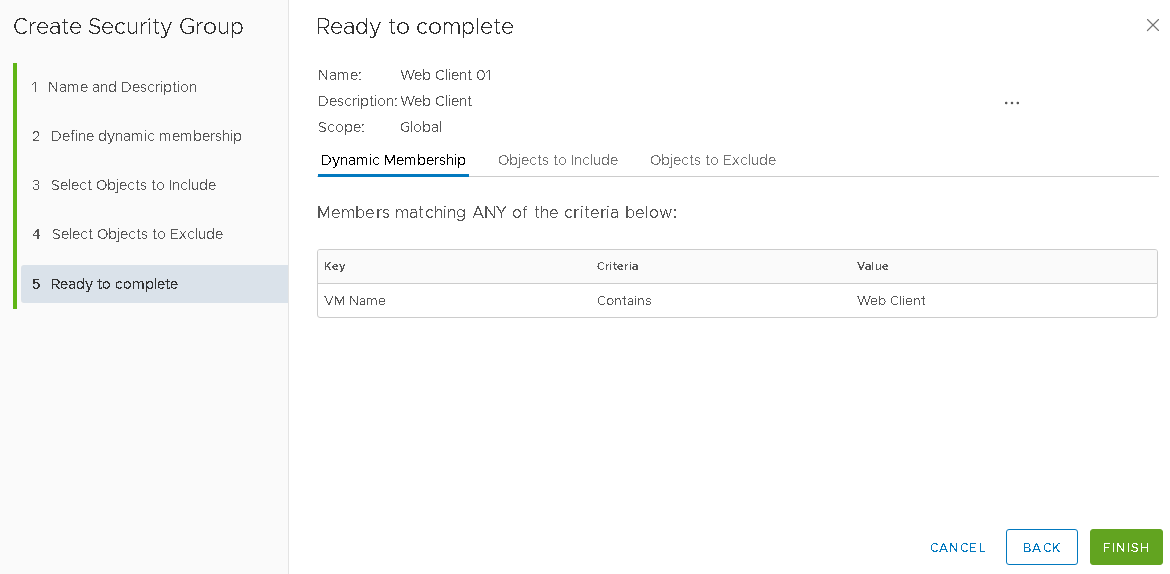
On the Dynamic Membership page, use VM Name, Contains Web-App which will automatically allow the VMs to be available in a group with the mentioned condition, Clik Next
Click Next
Click Next
Click on Finish
Next, we have to create firewall rules to configure the micro-segmentation between the virtual machines
Firewall Configuration
Navigate to Firewall From general option expand default Section
There will be default rules and you have the option for allow or block
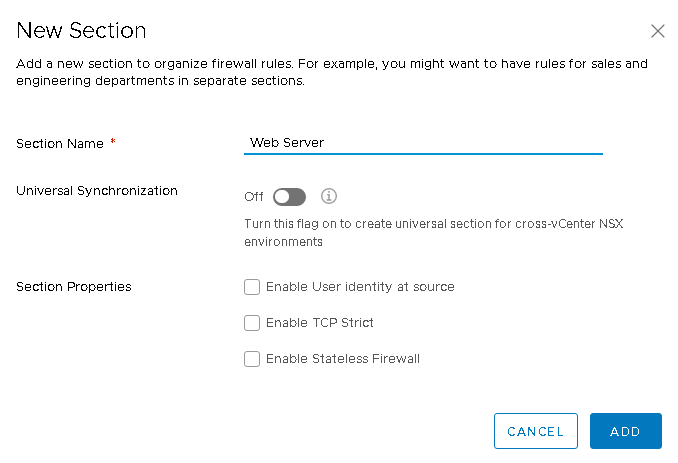
Click on ADD SECTION
Provide a Name and Clik on Add
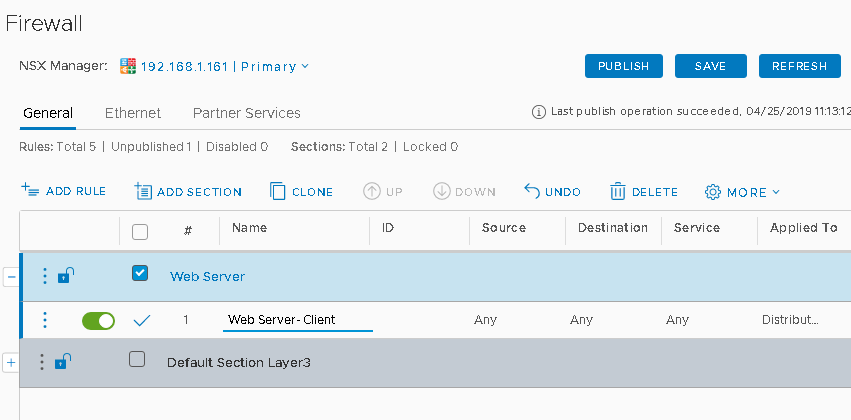
Select the newly created section on click on add rule
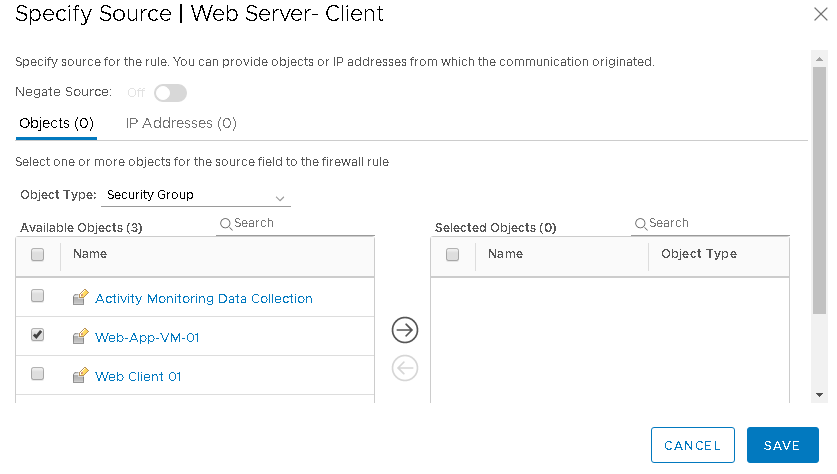
Provide a name to the rule and specify the source by click on Any under Source Tab
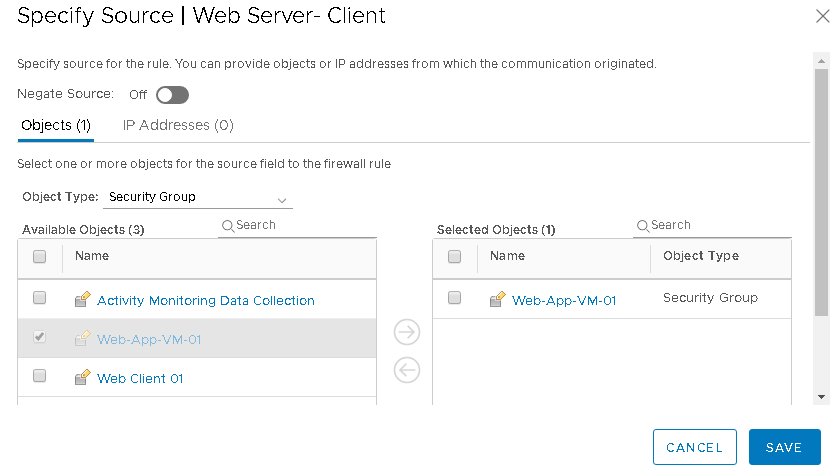
From Source Object Screen select the security group created before and added to selected objects Column and Clik on Save
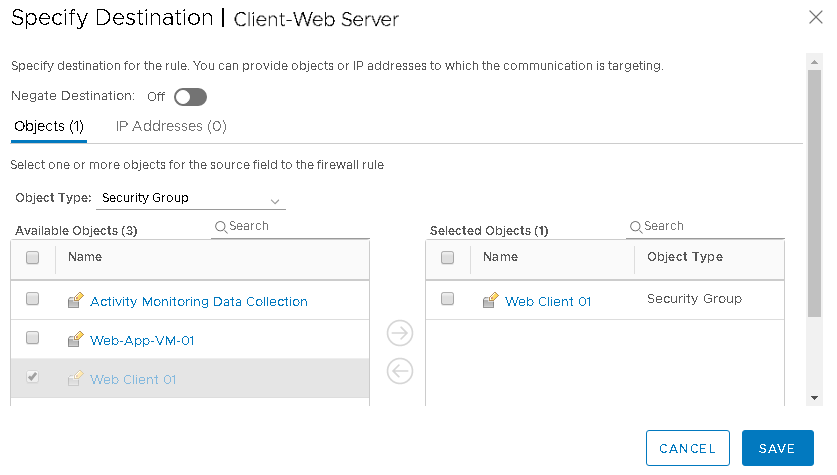
From Destination, Object Screen select the security group created before and added to selected objects Column and Clik on Save
You can follow the same procedure for creating multiple rules to configure micro-segmentation
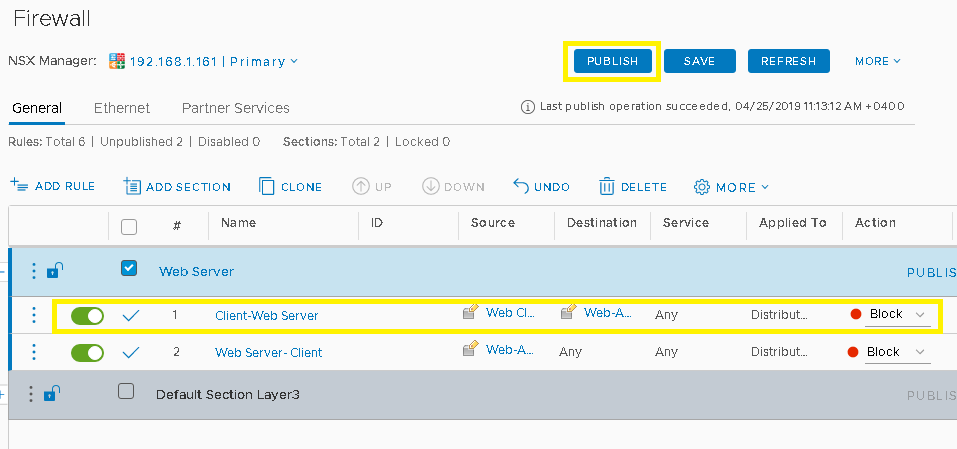
Once you created the rule Click on Publish
Conclusion
We have configured micro-segmentation in our environment, we have tested with blocking communication from Web Client to Web App servers also Web App to any here. You may create multiple rules allow or block traffic between your virtual machines. NSX based micro-segmentation enables to increase the agility and efficiency of your data center while maintaining an acceptable security posture.