
In this post I will be sharing the information on replacing self-signed certificate by a Certificate Authority (CA) signed SSL certificates in a vSphere 6.7 environment. VMware has pre-packaged the vSphere Certificate Manager utility to automate the replacement process.
The vSphere Certificate Manager utility provides all workflows to replace or regenerate the Machine SSL Certificate, Solution User Certificates and the VMCA Root Signing Certificate on the vCenter Server and Platform Services Controller.

Before starting the procedure just a quick intro for managing vSphere Certificates, vSphere Certificates can manage in two different modes
VMCA provides all the certificates for vCenter Server and ESXi hosts on the Virtual Infrastructure and it can manage the certificate lifecycle for vCenter Server and ESXi hosts. Using VMCA default the certificates is the simplest method and less overhead.
This method will replace the Platform Services Controller and vCenter Server Appliance SSL certificates, and allow VMCA to manage certificates for solution users and ESXi hosts. Also for high-security conscious deployments, you can replace the ESXi host SSL certificates as well. This method is Simple, VMCA manages the internal certificates and by using the method, you get the benefit of using your corporate-approved SSL certificates and these certificates trusted by your browsers.
Here we are discussing about the Hybrid mode, this the VMware’s recommended deployment model for certificates as it procures a good level of security. In this model only the Machine SSL certificate signed by the CA and replaced on the vCenter server and the solution user and ESXi host certificates are distributed by the VMCA.
Note :- If you don’t have a template Refer this Post for creating a new Template
Login to vCSA by using SSH or Console and launch the bash by typing Shell.

Run /usr/lib/vmware-vmca/bin/certificate-manager and select the operation option 1

Enter administrator credentials and enter option number 1.
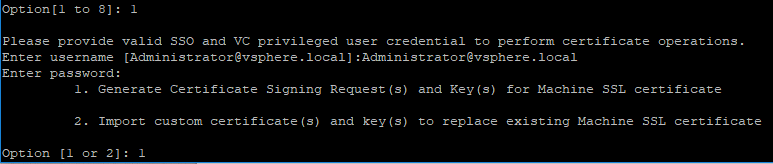
Specify the following options:

Once the private key and the request is generated select Option 2 to exit
Next we have to export the Request and key from the location , we will user win scp for this operation .
To perform export we need additional permission on VCSA , type the following command for same
#chsh -s /bin/bash root
![]()
Once connected to vCSA from winscp tool navigate the path you have mentioned on the request and download the vmca_issued_csr.csr file .

Open the Certificate Server URL using this format http://FQDN or IP /CertSrv/ from browser and select Request a certificate option

Select Advanced certificate request

Open the exported vmca_issued_csr.csr file in a notepad and copy the contents and paste ob the Column Based-64-encoded certificate Request , Select the appropriate Certificate template , here I choose vSphere 6.7 and Click on Submit

From Next Page Select the Base 64 encoded option and Download the Certificate and Certificate Chain

Note :- You have to export the Chain certificate to .cer extension , by default it will be PKCS#7
Open Chain file by right click or double click navigate the certificate -> right click -> All Tasks -> export and save it as filename.cer

Navigate to Certificate Authority Option and verify the status of request from Issued Certificate

Next you have export the newly downloaded certificates to vCenter Appliance
Login to vCenter appliance using winscp and copy to location .
Note:- Remember path where you copied the new certificates , it is required for replacing menu .

Login to vCenter Server Appliance Console or using putty
Run /usr/lib/vmware-vmca/bin/certificate-manager and select the operation option 1

Enter administrator credentials and enter option number 2

Add the exported certificate and generated key path from previous steps and Press Y to confirm the change

Note:- If you are providing different certificate instead of chain certificate in Custom certificate for machine SSL option you will get error with "depth lookup:certificate"
It will take little time to complete and you can see message
Status : 100 % Completed [All tasks completed successfully]

Now Connect to the vCenter using Web Client and you can see the new custom certificate
