
Microsoft is coming with many more supporting features for Azure and they are growing very fast . In this post we just share now feature availability Immutable Storage for Azure Storage Blobs and some information about this Immutable Storage.

You may think what is mean by Immutable Storage and what is the purpose of this , When using immutable storage, no one can delete or alter your data–not even a systems administrator.
Let’s check what Microsoft says about what they offers with Immutable Storage
Financial Services organizations regulated by the Securities and Exchange Commission (SEC), Commodity Futures Trading Commission (CFTC), Financial Industry Regulatory Authority (FINRA), Investment Industry Regulatory Organization of Canada (IIROC), Financial Conduct Authority (FCA), and more are required to retain business-related communications in a Write-Once-Read-Many (WORM) or immutable state that ensures they are non-erasable and non-modifiable for a specific retention interval. The immutable storage requirement is not limited to financial organizations but also applies to industries such as healthcare, insurance, media, public safety, and legal services.
Today, we are excited to reveal the general availability of immutable storage for Azure Storage Blobs to address this requirement. The feature is available in all Azure public regions. Through configurable policies, users can keep Azure Blob storage data in an immutable state where Blobs can be created and read, but not modified or deleted.
Typical applications include:
Immutable data is priced in the same way as mutable data and there is no additional charge for using this feature. Please refer to the Azure Storage Pricing page for the related pricing details.
To use this feature you must create a General-purpose v2 (GPv2) account through the Azure Resource Manager. You can test or enable this feature using below procedure
Note:-The container must be in a GPv2 or blob storage account.
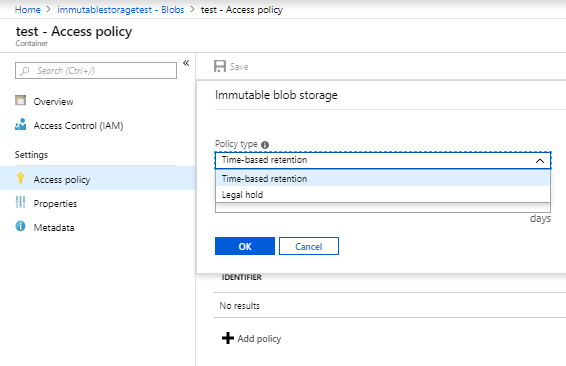
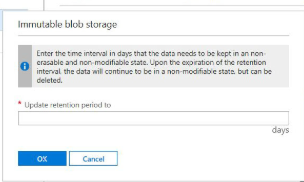
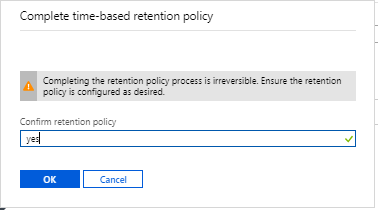
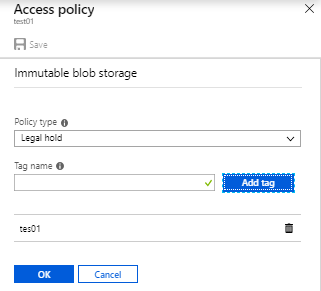
Initial state of the policy will be in unlocked and you can change to the policy before you lock it. Locking is essential for compliance with regulations like SEC 17a-4.
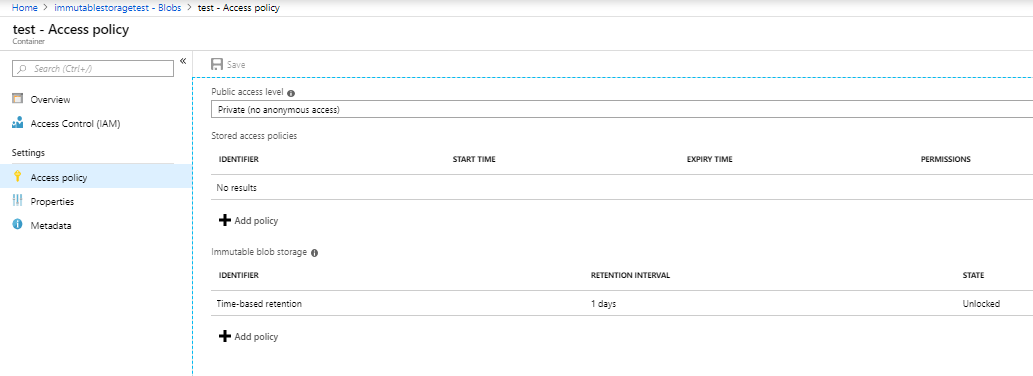
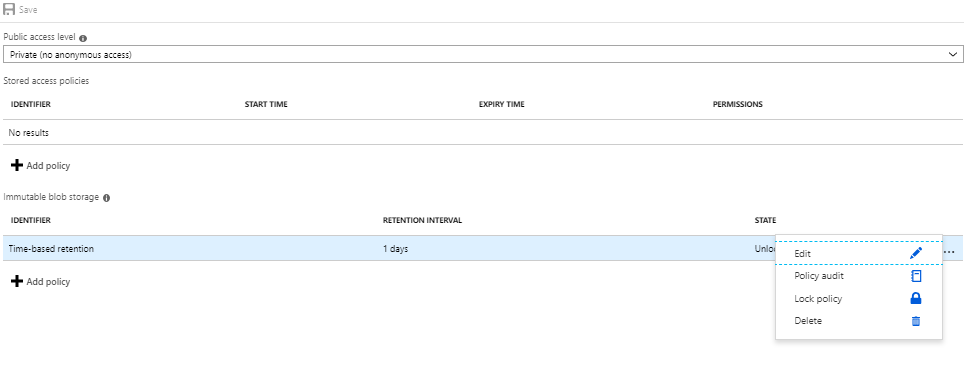
You have type ” yes ” to confirm and click to get activate the policy . After the policy is locked, it can’t be deleted, and only extensions of the retention interval will be allowed.
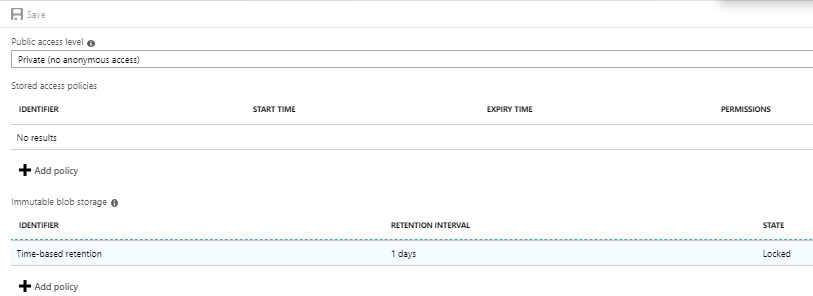
After enabling the your window will look like below image .
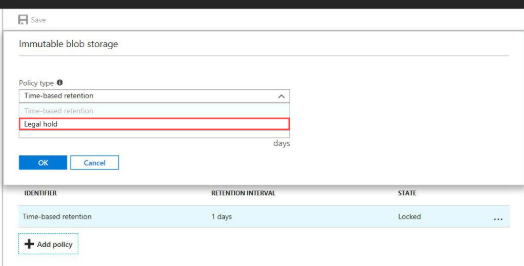
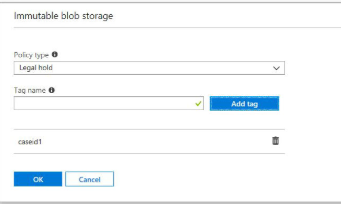
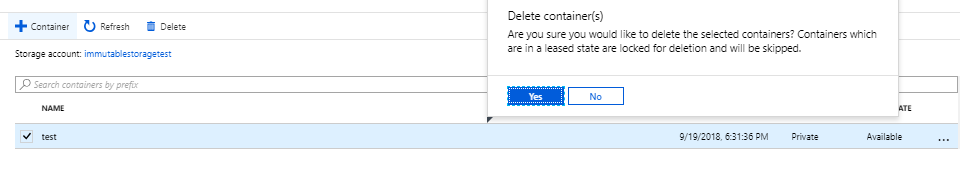
Select container we created with policy and click on Delete , it will give a message shown below , lets click on ” yes “ to continue
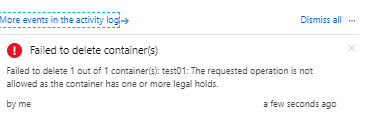
And it failed , as it cannot be deleted since it is a Immutable Storage , Message shows like below image.
Immutable Storage for Azure Storage Blobs is supported in the Azure Portal, the .net Client Library (version 7.2.0-preview and later) the node.js Client Library (version 4.0.0 and later), the Python Client Library (version 2.0.0 and later) and the Java Client Library. Preview support is available in CLI 2.0, and PowerShell (version 4.4.0-preview) with production support coming very soon.
You can also directly use the Storage Services REST API. This feature is supported on Blob Service REST API version 2017-11-09 and later and on Azure Storage Resource Provider REST API version 2018-02-01 and later. In general, we always recommend using the latest versions regardless of whether you are using the feature or not.
Reference 02