How to Create A Site to Site (S2S) VPN In Azure
A Site-to-Site VPN gateway connection is used to connect your on-premises network to an Azure virtual network over an IPsec/IKE (IKEv1 or IKEv2) VPN tunnel. Site-to-site VPN can provide better continuity for your workloads in hybrid cloud setup with AZURE. From the Azure side, we have to create a VPN gateway which will be used to connect from on-premise VPN device.
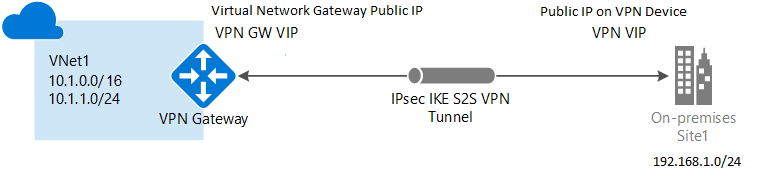
A VPN gateway is a type of virtual network gateway that sends encrypted traffic between your virtual network and your on-premises location across a public connection. You can also use a VPN gateway to send traffic between virtual networks across the Azure backbone.
In this post, we will discuss how to set up a site-to-site VPN
Prerequisites
- Valid Azure Subscription
- Supported VPN device in On-Premises
- Static Public IP address on VPN Device
Steps involved in creating a site to site VPN
- Create a Virtual Network
- Create Gateway Subnet
- Create Virtual Network Gateway
- Create Local Network Gateway
- Add Connection for Site-To-Site VPN
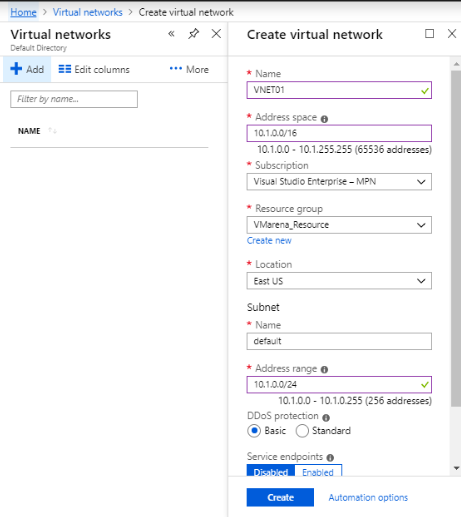
Create a Virtual Network
An Azure Virtual Network (VNet) is a representation of an on-premise network in the cloud. This means that we can create one or more subnets for Virtual Machine(s) or other Azure services.
- Log in to the Azure portal.
- Navigate to Virtual Networks and click on create
- Add the required information on the VNet creation page.
Name: Name for the VNet
Address Space: IP range for the VNet. If you have multiple Address ranges, it can add later
Subnet name: Name for the subnet you like to add
Subnet Address range: Subnet IP range (it must be within the Address Space listed before)
Resource Group: select the existing group or Can create a new group
Location: location of the VNet
- Click on create to continue
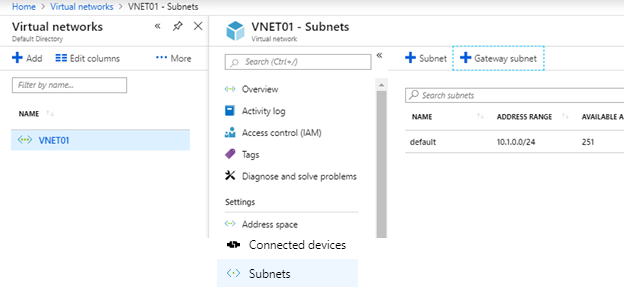
Create Gateway Subnet
Navigate to Virtual Networks and Select the VNET we created in the previous step and Click on subnets.
- Click on gateway subnet option
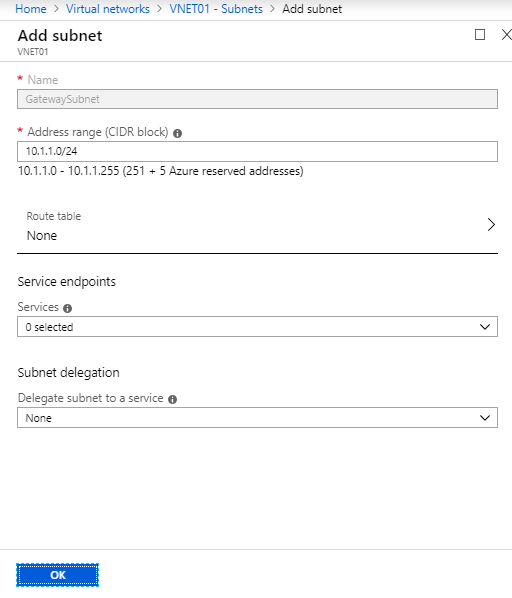
- Define the subnet for the gateway and click OK
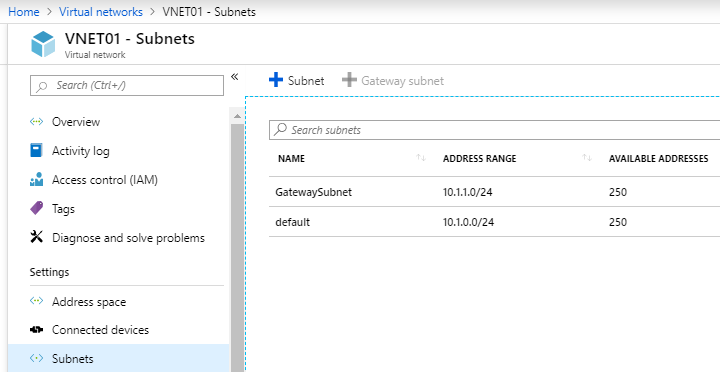
- Once created Gateway Subnet you can see that on Subnet page
Create Virtual Network Gateway
- Navigate to from All Services -> Networking ->Virtual Network Gateways
- Click on Add button to create a new virtual network gateway
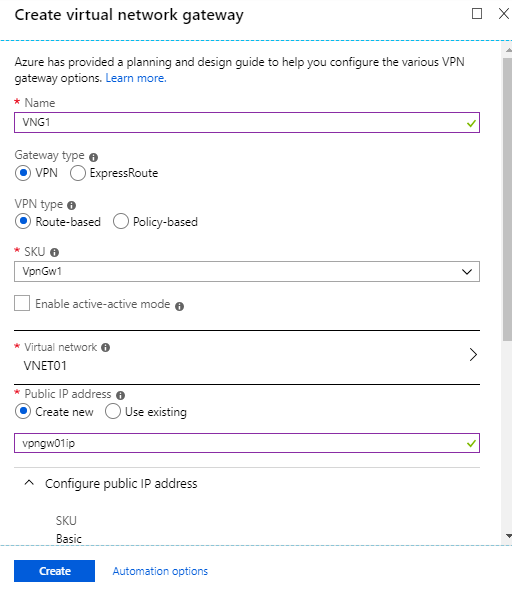
- Add the required details to each fields and click on Create
Name: Name for the virtual network gateway
Gateway Type: For our VPN it will be VPN
VPN Type: Type of the VPN (Route based or POlicy Based ) we choose route-based since it is a regular one
SKU: SKU for the VPN type
Virtual Network: Select the VNet you have created following the previous step
Public IP Address: VPN need to have a public IP address. Select public IP from here or if you don’t have, once you click on the option it will allow you to add a new one
Location: Select the correct region to match with VNet region
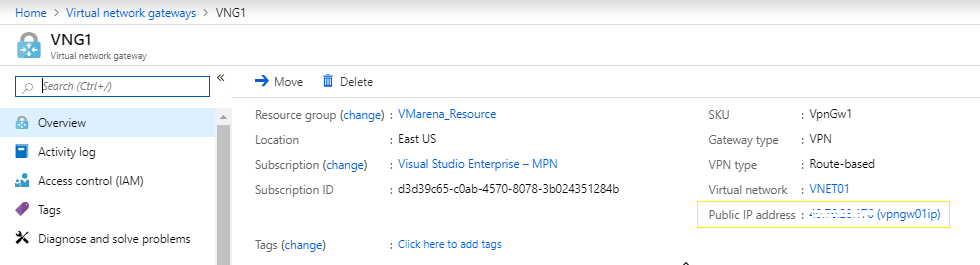
It will take some time to complete the task and once it’s done you can see the public IP address details. This Public IP will be added to your configuration in the on-premises VPN device
Create Local Network Gateway
Local Network gateway which represents your local network.
- Navigate to from All Services -> Networking ->Local Network Gateways
- Click on Add button to create new Local Network Gateway
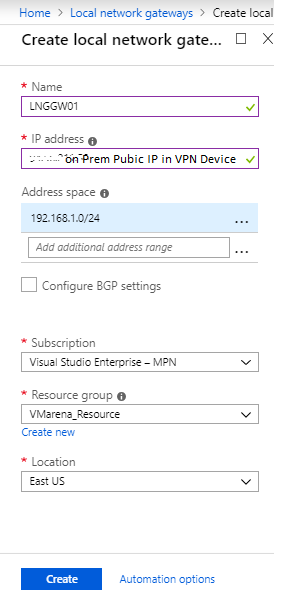
- Add the required details to each field on the local network gateway creation page
Name: Name for the local gateway
IP Address: Public IP address to represent your VPN device.
Address Space: On the premises address ranges. You can add multiple ranges.
Resource Group: Create new resource group or use the same one you were using
Create a Connection – Site to Site VPN
In this step, we will create a Site-to-Site VPN connection between your VPN device and the virtual network gateway.
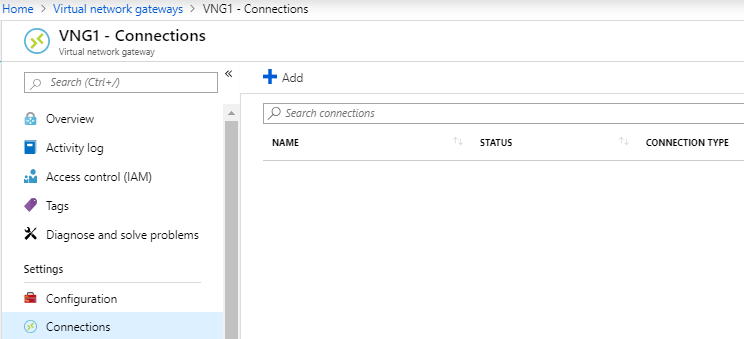
- Navigate to the Virtual network gateways and Select previously created, Select Connection option under the settings tab

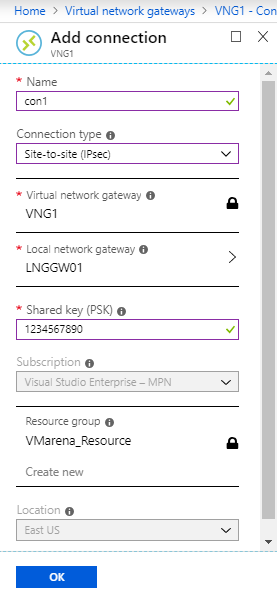
- Provide the required details on each field
Name: Name of the connection
Connection Type: Type of the VPN (site-to-site(IPsec)
Virtual Network Gateway: Select the relevant virtual network gateway
Local Network Gateway: Select the relevant local network gateway for your connection
Shared Key: Pre-shared key you going to use for the VPN configuration, use a complex we have used a dummy one
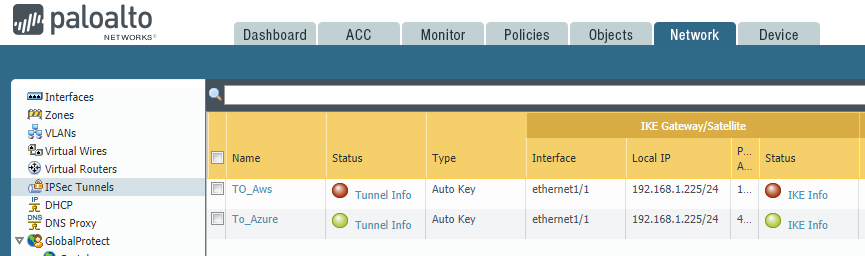
Next configuring the VPN Connection in your on the premise VPN device, and you will see the connection is active from your firewall device. In our scenario, we use Paloalto Firewall to create the VPN tunnel and our Tunnel To_Azure VPN is up.
We referred to
PA KB for creating Tunnel
Once VPN connectivity made from on-premise VPN device you can see the status on Virtual network gateways -> Connections option
Conclusion
We have successfully created a site to site VPN connection from Azure network to On-premises and you can follow the same step if you want to create a connection. Few points you have to check before proceeding this, please involve your network and security team to understand the networking details and security things before. Now you can create VM in Azure and map to this VNET and start accessing, we will be sharing another post soon on the same.